Calculating a cybersecurity budget

Security and spending
What is the required minimum cybersecurity budget? How should budgets be structured and allocated? And what are the impacts of falling short?
In the UK we are becoming familiar with new rules in force to ensure British companies are cyber-secure. Threats grow worse each year. Just as Moore's law applied to transistors and therefore computing power, so it is with cybersecurity risks which grow exponentially year on year at a nominal rate of at least 10 percent.
An oft quoted figure from Cybersecurity Ventures puts the global cost of cybercrime at £6.5T in 2023 and predicts a rise to £8.3T in 2025. These risks track our increase in computer use over the past 40 years. Over 27 percent of companies experience cyber-attacks on a weekly basis. Once an attack begins, things usually escalate as business details are exchanged between criminals.
The bigger the company and its financial growth, the bigger the risk. Companies should match investment in cybersecurity with size and risk to keep business operations safe from criminal activity.
Unfortunately, some British businesses are struggling to budget at the correct level. In some cases they do not budget anything at all. Some companies with yearly profits over £30m have no cyber budget whatsoever!
On the flip side I have found some of the strongest and most secure IT systems within very small businesses ranging from small manufacturers to local charities, all of whom had excellent cybersecurity but tiny budgets. How can this be?
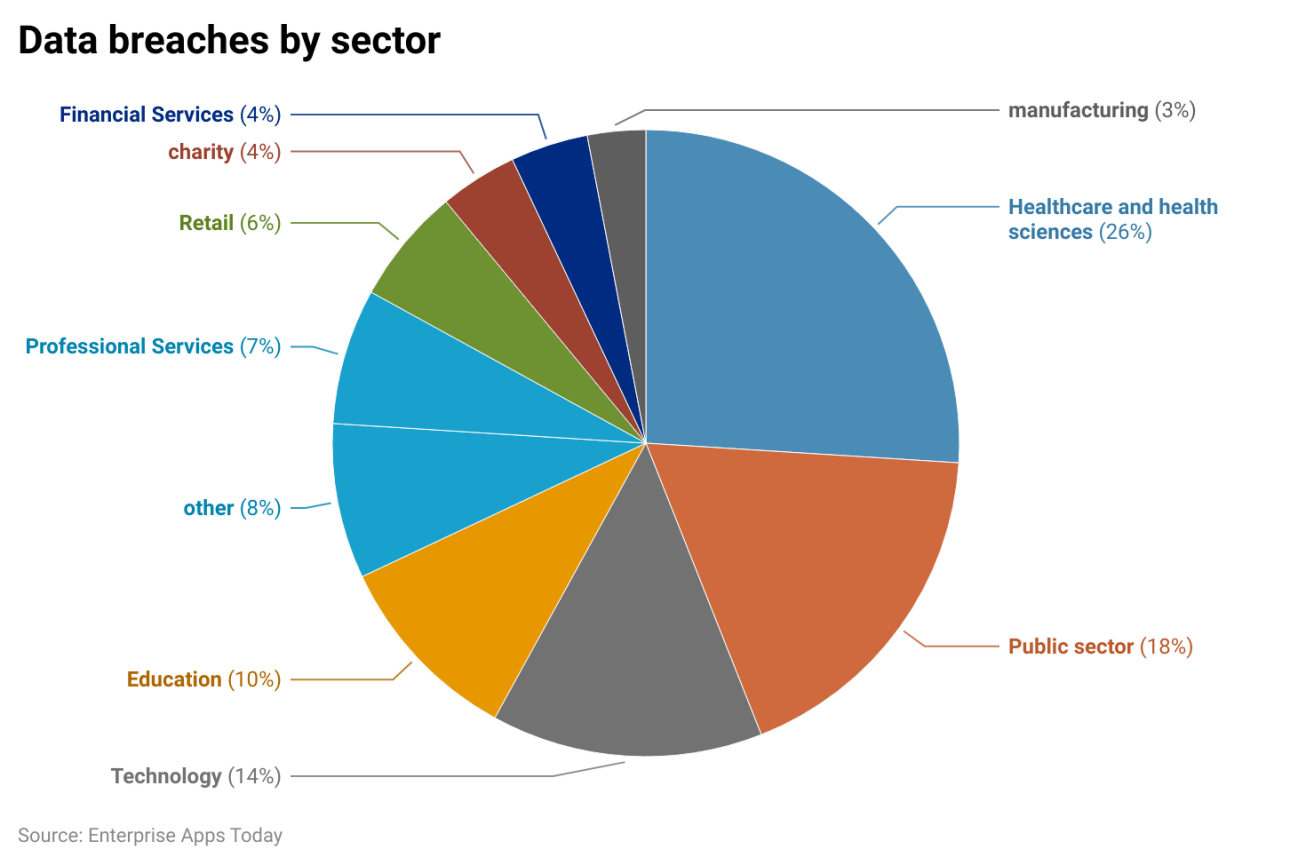
Figure 2: Data Breach Statistics 2023 and Facts: Enterprise Apps Today
Communication costs
From experience I know that cybersecurity risks are hard to understand outside of tech circles. Perhaps the fault lies with us experts for being poor communicators?
Cybersecurity is a complex and demanding profession, encompassing areas of computer science, law, psychology, mathematics, politics … even physics and quantum mechanics come into our daily thinking!
It is our duty, but also a struggle to distil, present and share complex yet accessible information to businesses and the public.
None of that information is any use if you cannot ingest and process it. Thousands of businesses pay for advice, reports, pen-tests and risk evaluations that go straight to a shelf or filing cabinet.
But these are not "bankable" resources there for later reference. It is most valuable at the time you get it, and depreciates in value each day it sits around on a desk.
So think about the time budgets to be set aside to read and evaluate new information. Right now you are reading this blog post, which is time well spent toward your security posture. This kind of research needs formalising and budgeting for. Someone in your company should have some designated work hours set aside for staying up to date with cyber threats and using research statistics to understand more.
A significant cost is therefore a skill and knowledge cost. Do companies have a cybersecurity officer who can interpret threat information? What is the baseline salary for that? What support costs does that role entail, like journal and intelligence access, travel and conferences?
Weighting risk information
Where is the balance between cautiously underplaying risks so as not to cause a alarm, inhibit daily business, and waste money on unnecessary defence, or painting too rosy a picture that leaves targets unprepared?
This is important because some might say "you can never spend too much on cyber-security". And they'd be wrong. There is such a thing as too much security. For example, you may have measures in place to protect assets or systems that you no longer use.
In reality though, most of us don't do enough. Finding the optimal sweet-spot is essential.
One hidden costs of cyber-security is misplaced and inappropriate security that saps the business in red-tape over-cautious and over-compliant behaviours. Over-caution can be a distraction from daily business.
For example, from the Cyber Security Breaches Survey 2021
"Two in five businesses (39%) report having experienced cyber security breaches or attacks in the last 12 months. Among the businesses that identify breaches or attacks, over a quarter (27%) are experiencing these issues at least once a week. However, only half of organisations have taken any action to help identify cyber security risks in the last twelve months."
That's a lot of information to digest. What does it mean? Should we expect and budget for a catastrophic breach every year with a two-fifths probability? If half of businesses are "getting away with it", can we factor in another fifty percent of slack into our risk model?
Delegating risk
It turns out the 50% of those not looking at risk comprise customers of managed service providers (MSP). It isn't that they simply elected to ignore risk, but chose a security model that rests on third-party cybersecurity services. If those services are good, then they may be in a stronger position than those with more detailed in-house analysis on which they have not acted.
However, most MSP offerings focus on only a small area of protection, mostly generic stuff like mail filtering to reduce phishing attempts, secure networking, anti-virus and firewalling. These provide a basic foundation but might not overlap much with the wider needs of the organisation.
Moving security outside the organisation has other downsides that might actually increase risks. For example, there is a principle agent problem, especially if buying-in security means sharing access to some of your most sensitive trade secrets, processes and data.
Generic security is obtained from generic block-lists and course-grained or naive rules like blocking websites and downloads based on popular reputation. All of this can harm communication and R&D. Many MSPs in-turn outsource security from companies like Cloudflare, Microsoft and Google, which can inject ethical and privacy issues into the equation.
There are few "one-size-fits-all" solutions that are really much good if you have anything but the simplest business needs. However MSP solutions are attractive because they set a fixed budget and service level.
Reactive and variable costs
Reactive cybersecurity waits for something bad to happen to systems or data before it deals with the situation. Budgets get allocated after the horse has already left the stable.
It can work for a short time for smaller companies. Especially if they get a run of good luck. But as companies grow so do the type of cyber-attack they face. Rather than generic attacks they start to face tailored assaults.
Once a company has a substantial yearly profit it is a highly sought after target for criminal gangs worldwide. It's legally hard for companies to hide profit of course, and so there is no "flying under the radar". Assume that cybercriminals know at least as much as the tax-man.
On a positive note, we can use that threat-knowledge to scale spending in proportion to profit, and it's a very good rule of thumb. As a simple exercise, look at your spending on cybersecurity in past years alongside gross profits, and scale next year's spending in proportion.
The risks are not just loss of service, but quite terrifying fines that governments have brought in to force companies toward better security.
Figure 3: Malware gangs love open source offensive hacking tools: ZDNET
Post-attack costs
Cybersecurity budgets need to cater for the reactive and pro-active security. Many companies forget it's best to plan with trouble in mind. Keeping a pot of money aside for the worst case scenario, like large fines, might be wise. Alternatively a cyber insurance policy that covers incident response costs might be frugal.
What happens after an attack? You may be involved in lengthy investigation. It's necessary to find out what data has been lost or damaged, which systems may still be compromised.
Some companies want to play a blame game, both internally to find out whose "fault" it was, and externally to attribute an attack to a known actor. While we think these are usually pointless expenses, many leaders only feel better once they can say "The Russians did it" or "It was an insider job". That might become materially relevant if a criminal investigation ensues.
More important is getting everything back up and running again. Also, making sure the same thing isn't going to happen almost immediately You will need a post-attack analysis. This includes log and network analysis, bug identification, patching and updating. It may mean additional down-time for systems you already urgently want back online. That may mean renting additional servers while investigations continue.
Pre-attack spending
Whether attacks happen or not, there is always a quiescent cost to digital security. It is a foolish leader who says, "We haven't had a cyber-security problem for five years, so let's cut defence spending."
Ongoing work includes risk assessment, system evaluation, monitoring activity, protecting data, minor incident reporting and investigation, backups and other data management.
Most important of all is maybe threat intelligence. The world is changing and new threats emerge all the time. How does AI affect your security position?
This kind of work can be tedious and long. A good way to lower costs is to know your organisation well, to know its exposure and attack surface, vulnerable people and so on. This is a long game, to slowly build up an accurate picture of your assets, skills, processes, and all their weaknesses. Budgets for this kind of thing are best as 2, 5 and 10 year plans.
Pro-active security
One essential element of quiescent spending is "pro-active" work. This is not something covered under a software and MSP security contracts. Like post-attack security work, pro-active security takes place inside your company and must be carefully tailored.
The best analogy is to think of it like preventative medicine, which requires exercise and diet.
A common misunderstandings is that the technical side is all that cybersecurity entails. In fact the technology side only covers about 50 percent of identifiable risks.
Half of all cybersecurity risks lie in employees. Training is a vital component. Digital literacy skills and digital behaviour awareness is a responsibility issue not dissimilar to health and safety.
2023 statistics from Secureframe found that 20% of data breaches involved social engineering, or tricking employees and that 82% of full breaches involved a human element, typically an operator error.
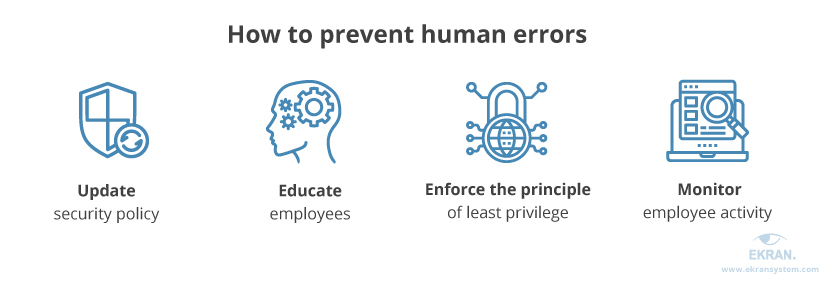
Figure 4: Human Errors in Cyber Security: Ekran System
Formalising cybersecurity
When new demands are made on businesses it is sometimes hard to see how they should be handled. Who should be responsible? Which department? If your company is small enough to have no 'departments' life is easier. Things like health and safety, diversity, quality might all be handled by a single person, maybe by the MD. In many cases though the law requires that a specific person take on formal responsibility as the officer.
Since half of cybersecurity is people-oriented, should it not be handled by HR? Then again, you may have a security department who would like to take charge of that sort of thing. Most people assume that because cybersecurity is all about computers it must be handled by IT.
We recommend that cybersecurity be managed independently from other departments. Businesses should set up processes and resources for cybersecurity as a distinct faculty, because much like quality it is a horizontal concern that touches every aspect of the business. In bigger companies the title that is emerging to describe that post is "CISO" - the Chief Information Security Officer.
Actually I think this is not broad enough, because cybersecurity is about more than just "information". Instead you may have a "CSO" who is the Chief Security Officer attending to all kinds of security including physical. But either will do. Structurally, like quality, cybersecurity should report directly to the top and not be placed 'under' another sub-hierarchy like IT.
The reason for this is that some of the gravest security risks come from the top. For example, directors may be able to bypass financial processes. That makes them targets for scams like deepfake phishing or blackmail.
Indeed I have worked for major banks and civic organisations where we conducted research yielding "inconvenient truths". We found that rather than low-grade employees being a risk it is upper management and directors whose behaviour is more worrying, because they can do more damage, often have a cavalier attitude toward security, take more risks and underestimate the impact of those risks compared to other employees. See this account of a $25m deepfake scam.
In terms of budget this requires creating a separately salaried position. As soon as you are able to, it pays to employ a cybersecurity officer who is singularly responsible for that domain. Without going into all the roles let's focus on one or two, specifically training.
Cybersecurity training
Working cybersecurity is bottom-up, not top-down. In other words it cannot be obtained by decree, imposition and tyrannical policy. There must be "buy-in" and we should be prepared to pay staff extra to shoulder any inconvenience or cost associated with security.
It should also be responsive and blame-free. All staff should have someone they can talk to, at any time, without fear, when they have questions, suspicions, concerns or problems around cybersecurity.
Ongoing staff training in cybersecurity should be accessible to all computer users. One should provide regularly scheduled refreshers because of the fluidity of the area. This is best tailored to the company, rather than generic "Don't click on strange links" seminars.
Think of this more like an internal security briefing. If the content of that briefing is the same year on year, it is probably lacking. Here, companies can make the mistake of buying-in cheap e-learning films and quizzes, but these are often ineffective learning tools.
If your CISO/CSO cannot provide this in-house, then spending the extra budget on an independent specialist trainer with decades of industry and educational experience is a much better approach to make positive behavioural changes across the company.
A good trainer obtains buy-in and commands attention. In-person training is to be done with practical exercises and demonstrations as the preferred form of delivery. I have experienced employees muting training videos, correctly guessing easy quiz answers, and days later causing cybersecurity incidents. In fact, training access and quality is a nationwide problem and contributes to a widening skills gap with digital skills sorely needed.
" Two-thirds (66%) of large UK businesses are struggling to recruit employees with the digital skills they need and three in five workers (58%) stating their employer has never provided them with training to improve their digital skills. " – Skills Gap Statistics UK 2023, Oxford Learning College, 2023.
Talking Budgets
So, with all this extra spending in mind, it's time to address the budget. Every business is different with industries such as technology spending on average 3% more than other industries.
Firstly, looking at the financial impact of losing digital assets, data, access and communication needs to be considered.
If we take for example, a local gardening business with physical marketing and telecommunications, the percentage budget is likely to be lower than for a manufacturer of similar size and profitability.
Very roughly what we are talking about here is the product of a a dependency tax and a complexity burden.
The more dependent a firm is upon technology for day-to-day running, the more risk it shoulders and the more it should spend. The more complex it is, in terms of processes, the higher the impact of any digital failure.
Since both businesses likely have a webstore or client database, both companies are still required to follow cybersecurity essentials as advised by the GDPR and will have the same basic responsibilities for data protection.
The latter company will have lists of suppliers and orders in the pipeline as well as just customers.
I suggest starting at the average budget for most businesses and adjusting up or down with consideration for an impact report, type of industry, data protection needs and internet usage.
The overall worldwide average for any sector was 9.9% of their total IT budget. We spend a little more in the UK at 22%, and it's 24% in US, with an increase of 15% across EU nations between 2021-2022 alone.
" The biggest spenders are tech and business services organisations. Organisations in these sectors spend just over 13% of their total IT budgets on cyber security.
Government organisations and financial services firms spent 9.6% and 9.7%, respectively. Following them were utility providers (8%), transportation (6.6%), and manufacturing (6.1%).
The lowest spend in the security benchmarking study was in education organisations which spent only 5.9% of their IT budget on cybersecurity. Healthcare is another notorious under-spender on security. " – SenseOn, 2022.
Given an IT spend of 10% these come to between 1.5% and 2.4% of total company budget. With such a rapid rate of growth we can see budgets reaching about 5% or more of total expenditure by 2026.
Where will this money come from?
The clue, as we explored earlier is that cybersecurity is not solely the concern of "IT". Breaches and incidents affect brand value, marketing, customer loyalty, employee morale and much more. That is why it may make sense to factor cybersecurity out of ICT and create new, independent budgets.
Impacts of under-spending
Notorious under-spending on security over time has led to a widely reported increases in attacks on both our educational facilities and NHS service, with some examples like wannacry, NHS patient data breach, attacks on schools, and student data breaches.
When it comes to the impact of low cybersecurity budgets there are many interesting statistics to share, but perhaps more useful is a personal account:
A case study
I took a role as an IT contractor a few years ago, for a business with yearly profits around £30m expecting to find between 5%-15% of a healthy IT budget spent on cybersecurity.
Instead, I found a company with only a reactive model for security and even that was sorely lacking. They proffered an attitude of "Well, we pay an MSP to route our traffic, so the job is done".
At that company not even the most elementary cybersecurity essentials were followed and there were almost no digital skills across the entire company.
The cybersecurity budget was non-existent and the IT budget was only 0.7% of company profits in total. After spending 12 weeks there attempting to establish some cybersecurity basics I met with resistance.
Things eventually came to a head when an easily avoidable cyber-attack took place. The third-party MSP missed the attack. Data was breached in moments.
The company response was cavalier and dismissive. I quickly realised that the extremely poor investment in cybersecurity would continue far into the future and only when even more severe incidents occurred, when millions had been stolen, personal data breached, jobs lost and large fines imposed would action finally be taken and budgets increase.
Some takeaways

Figure 5: Cybersecurity budgets before and after a breach
Though spending cannot predict for certain what risks exposure you have, here's a few thoughts to guide you:
If your company employs more than twenty people consider that it is time to budget specifically for cybersecurity.
If your cybersecurity budget derives entirely from IT, consider whether creating a separate, specialist cybersecurity office might help. This could take on tasks such as brand protection, physical access control, data protection compliance, training, research and lots more. Because modern versions of these tasks require high technical literacy it may free-up less technical staff in other areas and improve overall efficiency.
If your cybersecurity budget is lower than 5% of the IT budget the risk is very high for a cyber-attack.
If you save less than 3% of annual net profits as a buffer against incidents, or have no cyber insurance policy, consider that a risky position.
With the rate of attacks increasing it might be time to review and boost IT and security budgets in 2024.
Don’t forget to keep up with periodic risk assessments because as the company grows so will your cybersecurity requirements.
Good cybersecurity people are hard to find and there's a lot of competition for them, so it might also be time to put out a job advertisement for a cyber security analyst who can do some of this in-house for you, or to look for experienced trainers who can come in and help you develop a policy.